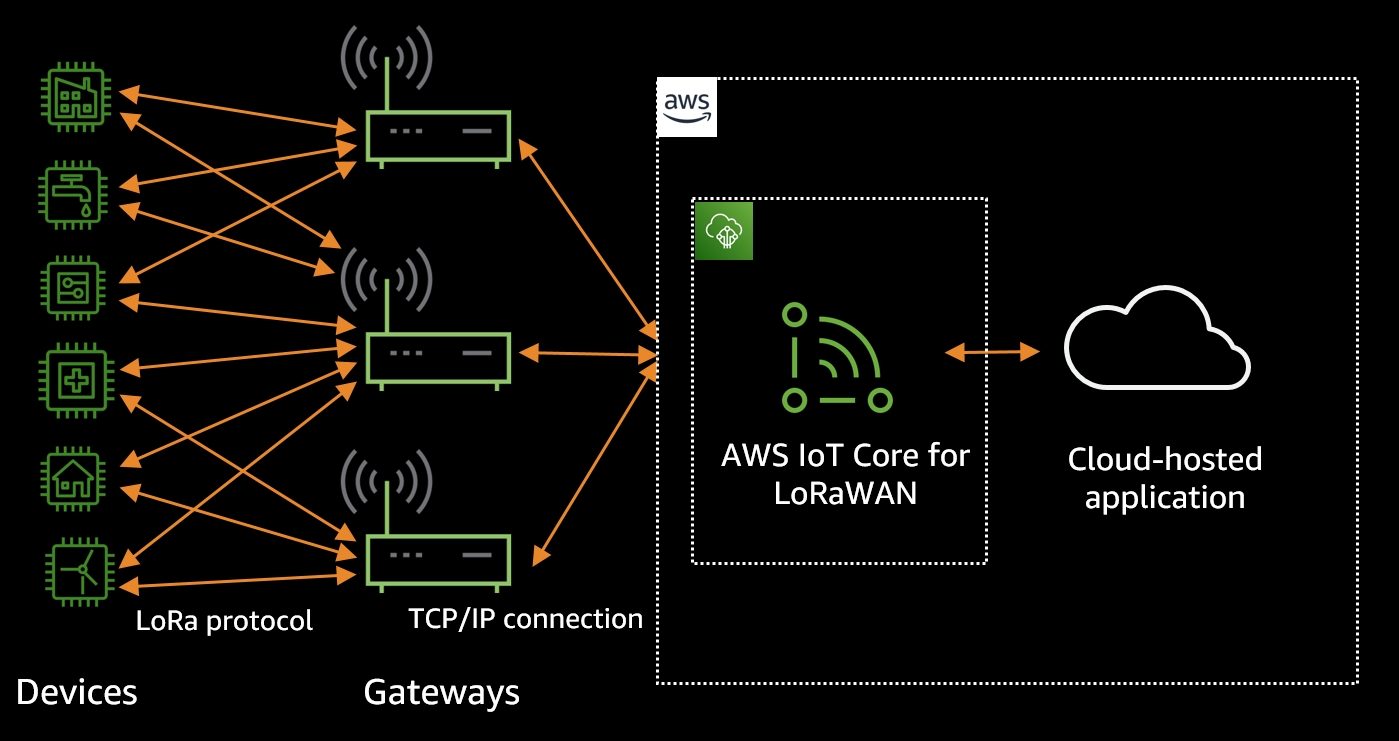
In today's digital landscape, the need for secure and efficient connectivity is more crucial than ever. As IoT devices continue to proliferate, businesses are increasingly faced with the challenge of securely connecting these remote devices to their Virtual Private Clouds (VPCs). This process, while essential, can be fraught with potential security risks and technical hurdles. Understanding how to securely connect remote IoT VPC is vital for safeguarding sensitive data and ensuring seamless operations.
The concept of securely connecting remote IoT VPC involves establishing a reliable and protected communication channel between IoT devices in the field and centralized cloud resources. This process not only requires robust security measures but also demands comprehensive planning and execution. By effectively implementing secure connections, organizations can leverage the full potential of IoT technology while minimizing vulnerabilities.
With the rise of cyber threats and data breaches, securely connecting remote IoT VPC is not just a technical necessity but a strategic imperative. Organizations that prioritize secure connectivity can protect their data assets, maintain operational integrity, and enhance customer trust. This article delves into the various aspects of securely connecting remote IoT VPC, offering insights into the best practices, tools, and strategies to ensure a fortified network infrastructure.
Table of Contents
- Introduction to Securely Connecting Remote IoT VPC
- Why is Secure Connectivity Important for IoT VPC?
- What are the Challenges in Securing Remote IoT VPC?
- Key Components of a Secure IoT VPC Connection
- How to Choose the Right Protocol for IoT VPC?
- Best Practices for Securely Connecting Remote IoT VPC
- Exploring VPN and Tunneling Options for IoT VPC
- How to Implement Multi-Factor Authentication in IoT VPC?
- Understanding the Role of Encryption in IoT VPC Security
- What Tools Can Enhance IoT VPC Security?
- Real-World Examples of Secure IoT VPC Connections
- How to Monitor and Maintain IoT VPC Security?
- Future Trends in Secure IoT VPC Connectivity
- Common Mistakes to Avoid in IoT VPC Security
- Conclusion: The Path Forward for Secure IoT VPC Connectivity
Introduction to Securely Connecting Remote IoT VPC
Securely connecting remote IoT VPC is a fundamental aspect of modern network architecture. As organizations deploy IoT devices across various locations, establishing a secure connection to VPCs ensures data integrity and operational continuity. This integration allows for efficient data exchange and centralized control, essential for scalable IoT solutions.
Why is Secure Connectivity Important for IoT VPC?
In the IoT ecosystem, secure connectivity is paramount. IoT devices often handle sensitive data, making them attractive targets for cyberattacks. Securely connecting remote IoT VPC protects this data from unauthorized access and potential breaches. Without secure connectivity, organizations risk data loss, operational disruptions, and reputational damage.
What are the Challenges in Securing Remote IoT VPC?
Securing remote IoT VPC presents several challenges:
- Device Diversity: IoT devices vary widely in capabilities and security features.
- Scalability: Managing a vast number of devices securely can be complex.
- Latency: Ensuring low latency while maintaining security is critical.
- Network Complexity: Integrating IoT devices with existing network infrastructure requires careful planning.
Key Components of a Secure IoT VPC Connection
To securely connect remote IoT VPC, several components are essential:
- Authentication: Verifying device and user identities to prevent unauthorized access.
- Encryption: Protecting data in transit and at rest to ensure confidentiality.
- Access Control: Defining permissions and roles to limit access to critical resources.
- Monitoring: Continuously tracking network activity for anomalies and potential threats.
How to Choose the Right Protocol for IoT VPC?
Choosing the right protocol is crucial for securely connecting remote IoT VPC. Factors to consider include:
- Security: Protocols should offer robust encryption and authentication mechanisms.
- Compatibility: Ensuring the protocol works seamlessly with existing infrastructure.
- Performance: Balancing security with network performance to avoid latency issues.
- Scalability: Supporting the addition of new devices without compromising security.
Best Practices for Securely Connecting Remote IoT VPC
Implementing best practices can significantly enhance IoT VPC security:
- Conduct Regular Security Audits to identify and address vulnerabilities.
- Use Strong Passwords and change them frequently to prevent unauthorized access.
- Implement Network Segmentation to isolate IoT devices from critical systems.
- Keep Software and Firmware Updated to patch security flaws.
- Educate Employees on cybersecurity best practices and potential threats.
Exploring VPN and Tunneling Options for IoT VPC
VPNs and tunneling protocols are popular solutions for securely connecting remote IoT VPC. They offer encrypted channels for data transmission, protecting it from interception. Common options include:
- IPsec: Provides secure, encrypted communication over IP networks.
- OpenVPN: An open-source VPN solution known for flexibility and security.
- SSL/TLS: Offers secure, encrypted connections over the internet.
How to Implement Multi-Factor Authentication in IoT VPC?
Multi-Factor Authentication (MFA) adds an extra layer of security by requiring multiple credentials. Implementing MFA in IoT VPC involves:
- Using Time-Based One-Time Passwords (TOTP) for device authentication.
- Deploying Hardware Tokens or Mobile Apps for additional verification.
- Integrating MFA with existing authentication systems for seamless operation.
Understanding the Role of Encryption in IoT VPC Security
Encryption is a cornerstone of IoT VPC security, ensuring that data remains confidential and tamper-proof. Key considerations include:
- Data Encryption: Securing data at rest and in transit with strong algorithms.
- End-to-End Encryption: Protecting data from the source to the destination.
- Key Management: Safeguarding encryption keys to prevent unauthorized access.
What Tools Can Enhance IoT VPC Security?
Several tools can bolster IoT VPC security:
- Firewalls: Protecting networks from unauthorized access and attacks.
- Intrusion Detection Systems (IDS): Monitoring for suspicious activity.
- Security Information and Event Management (SIEM): Aggregating and analyzing security data for actionable insights.
Real-World Examples of Secure IoT VPC Connections
Real-world implementations highlight the effectiveness of secure IoT VPC connections:
- Smart City Projects: Utilizing secure connections for efficient urban management.
- Industrial IoT: Ensuring safe and reliable operations in manufacturing environments.
- Healthcare IoT: Protecting sensitive patient data in connected medical devices.
How to Monitor and Maintain IoT VPC Security?
Continuous monitoring and maintenance are critical for IoT VPC security:
- Regularly updating security policies to address emerging threats.
- Conducting vulnerability assessments to identify and mitigate risks.
- Implementing automated monitoring tools for real-time threat detection.
Future Trends in Secure IoT VPC Connectivity
Emerging trends will shape the future of secure IoT VPC connectivity:
- AI-Powered Security: Leveraging artificial intelligence for advanced threat detection.
- Edge Computing: Reducing latency by processing data closer to the source.
- Blockchain Technology: Enhancing data integrity and transparency in IoT networks.
Common Mistakes to Avoid in IoT VPC Security
Understanding common pitfalls can help prevent security breaches:
- Neglecting Security Updates: Failing to apply patches can expose vulnerabilities.
- Ignoring Device Configuration: Default settings can be exploited by attackers.
- Overlooking Data Encryption: Unencrypted data is susceptible to interception.
Conclusion: The Path Forward for Secure IoT VPC Connectivity
Securely connecting remote IoT VPC is an ongoing process that requires diligence, planning, and the right tools. By understanding the challenges and implementing best practices, organizations can protect their networks and fully realize the potential of IoT technology. As threats evolve, staying informed and proactive is essential for maintaining a secure IoT ecosystem.
You Might Also Like
The Untold Story Of Surya Sethupathi's Age: A Journey Through TimeUnlocking The Potential Of Raspberry Pi VPC IoT: A Comprehensive Tutorial
Unveiling The Charismatic Charm: Cha Eun Woo Height And More
Exploring The World Of Bolly4u.org: A Comprehensive Guide
Exploring Movierulz Today: Insights Into The World Of Online Movie Streaming
Article Recommendations
- Everything You Need To Know About Vegamovies Dual Your Ultimate Guide
- Intriguing Duo The Dynamic Bond Between Will Smith And Jacob Scipio
- Angie Hermon The Rising Star In The Entertainment Industry